Incremental Mode
- Free Download John The Ripper
- John The Ripper Multi Core Competencies
- John The Ripper Multi Core Bits
- John The Ripper Multi Core I7
- John The Ripper Online
read https://www.openwall.com/john/doc/MODES.shtml
This is the most powerful cracking mode, it can try all possible character combinations as passwords. However, it is assumed that cracking with this mode will never terminate because of the number of combinations being too large (actually, it will terminate if you set a low password length limit or make it use a small charset), and you'll have to interrupt it earlier.
That's one reason why this mode deals with trigraph frequencies, separately for each character position and for each password length, to crack as many passwords as possible within a limited time.
John the Ripper is a free, easy to use, open source tool that takes the best aspects of various password crackers and unites them into one package. As such it can be harnessed by pen testers to. The nodes use an implementation of MPI called OpenMPI for communication and a version of John the Ripper program to calculate hashes. The modified version of John the Ripper used in this work enables the connection of different performances devices in the cluster to work together on password hash calculation using input from a wordlist file. To get hashcat and john up and running with multi-core is a little fiddly (it’s not download and crack), so I thought I’d document the setup and show some benchmarks with hashcat and John the Ripper utilising 36 cores. In order to select the 36 core instance you’ll need to use a HVM (hardware virtual machine) enabled machine image. For multi-CPU systems and multi-core CPUs, the c/s rates given are for one CPU core.For example, the Q6700 CPU achieves an equivalent of just over 2.5 million of traditional DES-based crypt(3) checks per second per core, but since this CPU is quad-core, this translates to just over 10 million of checks per second per CPU chip, with proper parallelization. We will need to work with the Jumbo version of JohnTheRipper. This is a community-enhanced, 'jumbo' version of John the Ripper. It has a lot of code, documentation, and data contributed by the user community. This is not 'official' John the Ripper code. It is very easy for new code to be added to jumbo: the quality requirements are low.
To use the mode you need a specific definition for the mode's parameters, including password length limits and the charset to use. These parameters are defined in the configuration file sections called [Incremental:MODE], where MODE is any name that you assign to the mode (it's the name that you will need to specify on John's command line). You can either use a pre-defined incremental mode definition or define a custom one.
Free Download John The Ripper
As of version 1.8.0, pre-defined incremental modes are 'ASCII' (all 95 printable ASCII characters), 'LM_ASCII' (for use on LM hashes), 'Alnum' (all 62 alphanumeric characters), 'Alpha' (all 52 letters), 'LowerNum' (lowercase letters plus digits, for 36 total), 'UpperNum' (uppercase letters plus digits, for 36 total), 'LowerSpace' (lowercase letters plus space, for 27 total), 'Lower' (lowercase letters), 'Upper' (uppercase letters), and 'Digits' (digits only). The supplied .chr files include data for lengths up to 13 for all of these modes except for 'LM_ASCII' (where password portions input to the LM hash halves are assumed to be truncated at length 7) and 'Digits' (where the supplied .chr file and pre-defined incremental mode work for lengths up to 20). Some of the many .chr files needed by these pre-defined incremental modes might not be bundled with every version of John the Ripper, being available as a separate download.
Using masks
read https://github.com/magnumripper/JohnTheRipper/blob/bleeding-jumbo/doc/MASK
Checking for GPU support
Cracking ZIP and RAR protected files
read https://dfir.science/2014/07/how-to-cracking-zip-and-rar-protected.html
How-to - Cracking ZIP and RAR protected files with John the Ripper
After seeing how to compile John the Ripper to use all your computer's processors now we can use it for some tasks that may be useful to digital forensic investigators: getting around passwords. Today we will focus on cracking passwords for ZIP and RAR archive files. Luckily, the JtR community has done most of the hard work for us. For this to work you need to have built the community version of John the Ripper since it has extra utilities for ZIP and RAR files.
For this exercise I have created password protected RAR and ZIP files, that each contain two files.
The password for the rar file is 'test1234' and the password for the zip file is 'test4321'.
John The Ripper Multi Core Competencies
In the 'run' folder of John the Ripper community version (I am using John-1.7.9-jumbo-7), there are two programs called 'zip2john' and 'rar2john'. Run them against their respective file types to extract the password hashes:
This will give you files that contain the password hashes to be cracked... something like this:
John The Ripper Multi Core Bits
After, that you can run John the Ripper directly on the password hash files:
You should get a message like: Loaded 1 password hash (PKZIP [32/64]). By using John with no options it will use its default order of cracking modes. See the examples page for more information on modes.
Notice, in this case we are not using explicit dictionaries. You could potentially speed the cracking process up if you have an idea what the password may be. If you look at your processor usage, if only one is maxed out, then you did not enable OpenMP when building. If you have a multi-processor system, it will greatly speed up the cracking process.

Now sit back and wait for the cracking to finish. On a 64bit quad-core i7 system, without using GPU, and while doing some other CPU-intensive tasks, the password was cracked in 6.5 hours.
John The Ripper Multi Core I7
Now if you want to see the cracked passwords give john the following arguments:
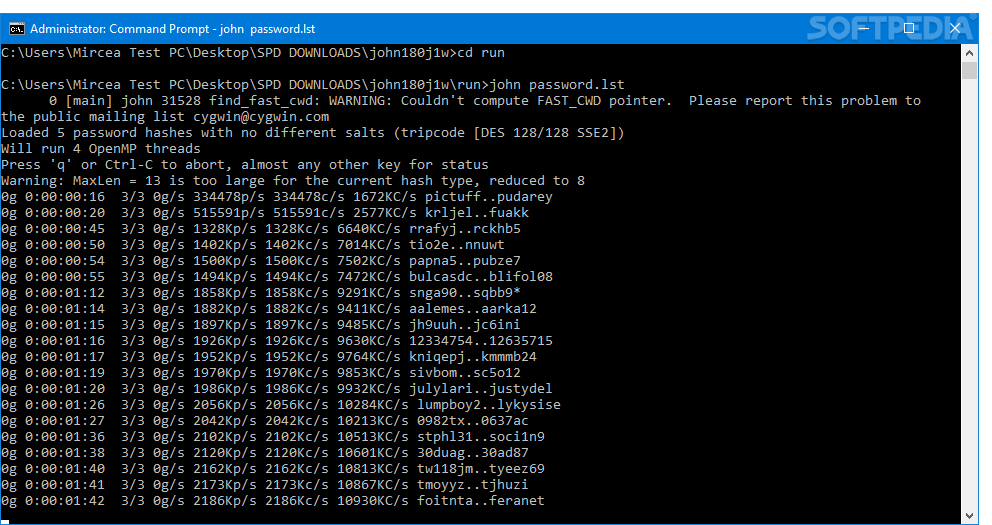
It should output something like:
Note: the hash file should have the same type of hashes. For example, we cannot put the rar AND zip hashes in the same file. But this means you could try to crack more than one zip/rar file at a time.
John The Ripper Online
For the rar file it did not take nearly as long since the password was relatively common. If you take a look at john.conf in the run directory, it has a list of the patterns it checks (in order). The pattern 12345 is much more likely than 54321, so it is checked first resulting in a quick crack.